This post has been republished via RSS; it originally appeared at: Core Infrastructure and Security Blog articles.
As you may have heard; Windows LAPS feature is released to Public Preview in the last week of April. It has support for two main scenarios for backing up local administrator password such as storing passwords in Azure AD and Windows Server AD. It also has interoperability with legacy LAPS solution. This article on the other hand; will focus on native cloud deployment for Windows 10/11 clients that does not have legacy LAPS client installed, managed through Intune and either Hybrid Azure AD Joined or Azure AD Joined.
In this blog post, I’ll walk you through basic policy configuration and core Windows LAPS functionalities such as accessing local administrator passwords from different consoles and manually triggering password rotation.
Pre-requisites for enabling Windows LAPS may change in the future, so it is always a good idea to check online documentation first; but the tasks we will cover in this post are as follows:
- Enabling local administrator password feature on tenant level
- Creating a Windows LAPS Policy
- Monitoring policy application
- Accessing local administrator passwords that are backed up
- Rotating local administrator passwords manually
Enable Azure AD Local Administrator Password Feature
Enabling Local administrator password settings in tenant level can be done in Azure AD portal, Devices node, Device settings view. Option to enable Azure AD Local Administrator Password Solution (LAPS) will be available for configuration.
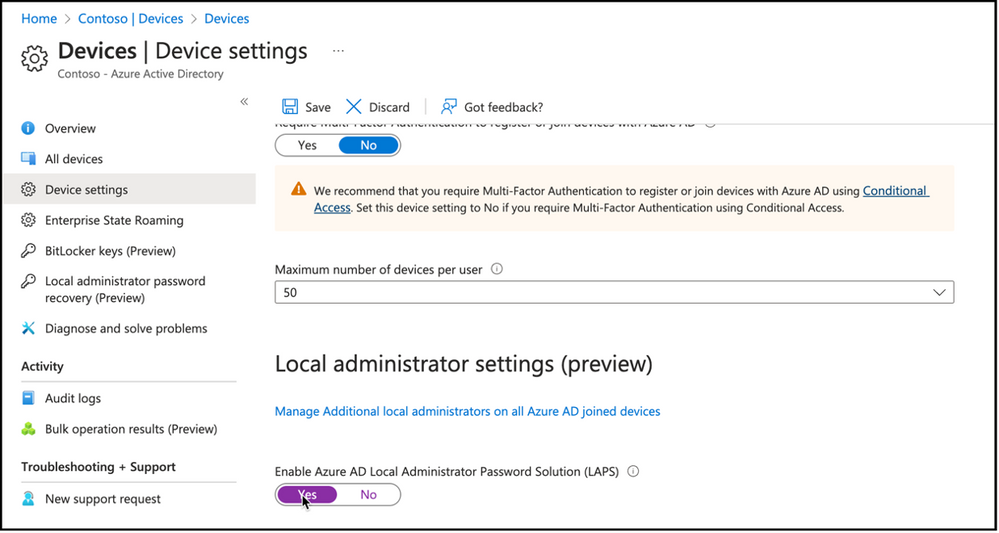
After enabling feature on the tenant level, we can proceed with policy creation.
Creating Local Admin Password Policy
Local Admin Password Solution policies can be configured from Endpoint Security Node, Account Protection view. Clicking on “Create Policy” button will present policy creation wizard.

First option will be selecting platform for the policy, and the second option will be policy type itself. As you notice, there are different account protection policy options such as Local User Group Membership or Account Protection as well as Local Admin Password Solution (Windows LAPS). Selecting Local admin password solution (Windows LAPS) from profile list will start policy creation wizard.

As always, first step is naming policy as well as giving a description.

Next step is building the policy itself. As you see there are several options regarding Administrator account, password options as well as the directory to backup the local administrator password. Let’s take a deeper look at these options and prepare our Windows LAPS policy.
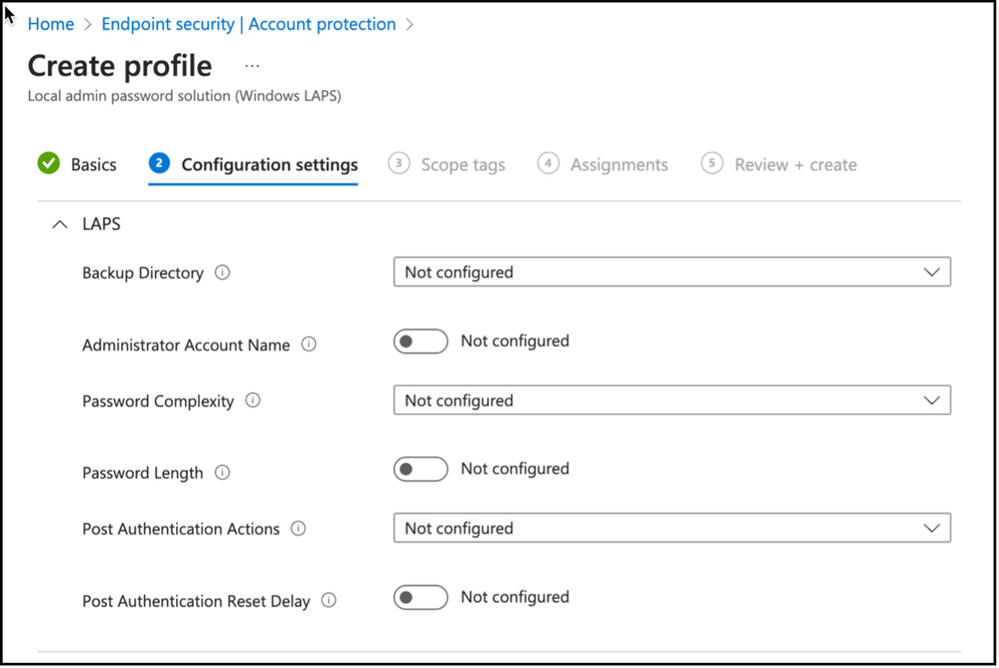
Backup Directory:
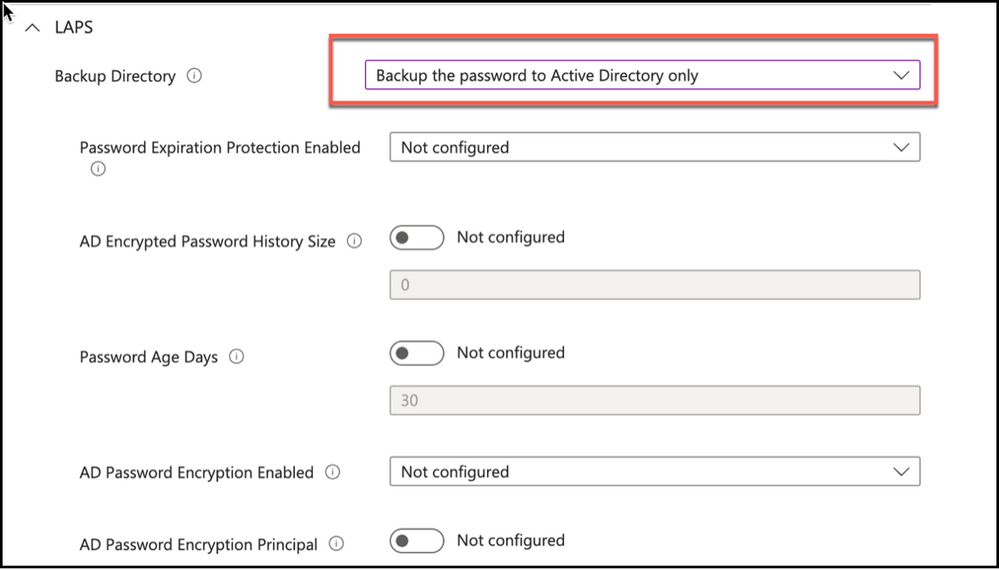
First setting in creating Windows LAPS policy is defining the directory service that will be used to backup the local admin password on the endpoints. It is possible to use Windows Server Active Directory or Azure Active Directory as a means to store local admin passwords. You can also use “Disabled” option to remove existing configuration.

There will be additional settings depending on the backup directory selected. Some of these will include Active Directory specific settings such as “AD Encrypted Password History Size”, “AD Password Encryption Principal” and “AD Password Encryption Enabled” if backup to Active Directory is selected.
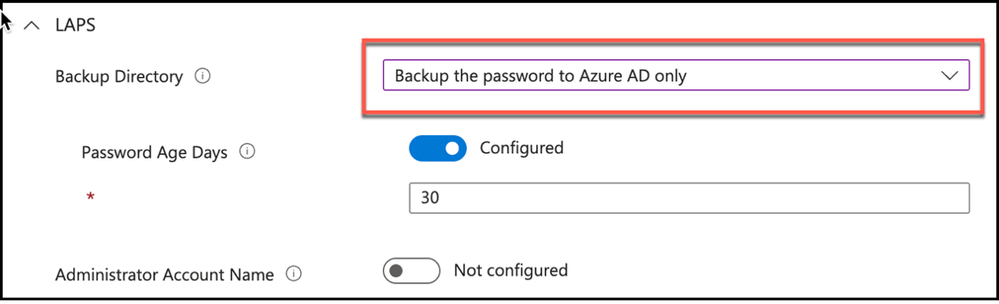
Only additional setting to configure will be Password Age Days when Azure AD selected as the directory service for backing up the local administrator password. Password Age Days option defaults to 30 days unless it is configured and it is possible to configure this option between 7 days & 365 days while backing up to Azure AD, and 1 day & 365 days while backing up to Active Directory.
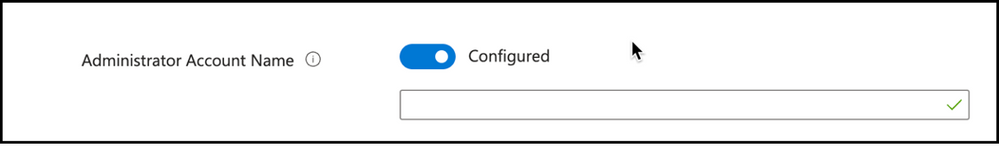
Administrator Account Name: Another setting to configure is the Administrator account name to manage. Policy will use Built-In Administrator SID if not configured. Renaming built-in administrator account will not impact SID monitoring, so you can configure this option to define, if there is another local administrator account present on the endpoint to manage its password.
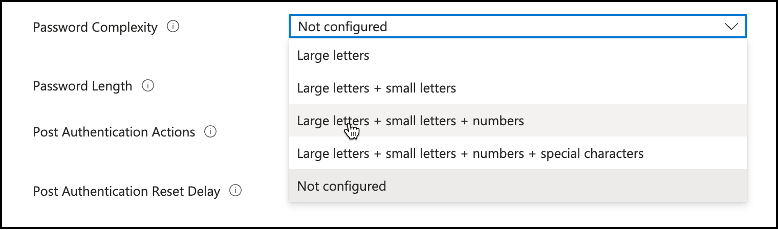
Password Complexity: Next setting that will require our attention will be Password Complexity. This is where we define how complex local administrator passwords will be on the endpoints. As you can see there are different options to use Large letters, small letters, numbers and special characters in the local administrator password.
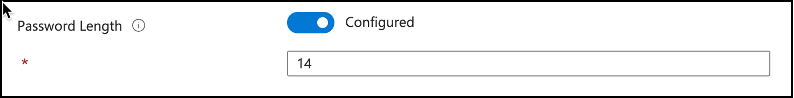
Password Length: Another important item to configure is the password length setting which will define the length of local administrator password created based on the complexity requirements defined earlier. It defaults to 14 characters unless defined, and has a minimum of 8 and maximum of 64 character limitation.
Post Authentication Actions: Post Authentication Actions will define what will happen to the password, user or device after logging on with the stored local admin credentials. Password will be reset at a minimum, managed account will be logged off or device will be rebooted after the expiry of grace period to make sure password rotation took place. Fort his configuration I will define my policy to reset the password and logoff the managed account upon expiry of the grace period.

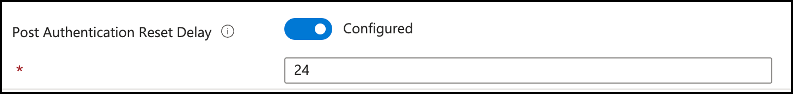
Post Authentication Reset Delay: Post authentication reset delay value will define the time in hours to execute the actions following authenticating with the managed identity as defined earlier. This setting defaults to 24 hours if not configured; and can be set between 0 (disables post authentication actions) and 24 hours.
Just like all the other device configurations that can be deployed by intune, next step in the policy wizard would be assigning a set of devices for policy application. In my environment i’ve used built in All devices group.

Monitoring Policy Application
It is possible to monitor Windows LAPS policy application via Intune just like any other policy. One way would be pivoting from policy itself. It is possible to view check-in status per logged on user in the policy details.

It is also possible to pivot from a device; checking device configuration view from device properties and validating the policy application to the endpoint.

When drilled through the device configuration applied, we can see per-setting level status as well. You may see the settings are successfully applied to our device in the following snippet.
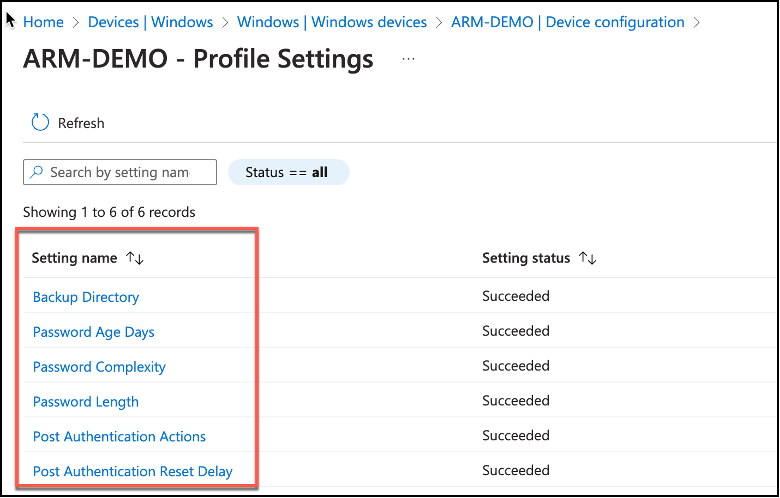
Accessing Local Admin Passwords
Once the policy is applied on the endpoint, Windows LAPS will create a random local administrator password for the managed credential in the endpoint and will store this as an attribute that is accessible through either Azure AD, or Microsoft Intune. On the other hand, there are some requirements for accessing the local admin password.
Someone who needs to view local admin passwords should be granted with the following rights in Azure AD as stated in the RBAC document here.
- microsoft.directory/deviceLocalCredentials/password/read
- microsoft.directory/deviceLocalCredentials/standard/read
An admin / operator user who has correct rights / roles assigned, can access to the local admin password recovery view either following Azure Local administrator password recovery view within Devices Node, ins Azure Active Directory console, or they can use “local admin password” view inside device properties within Microsoft Intune.
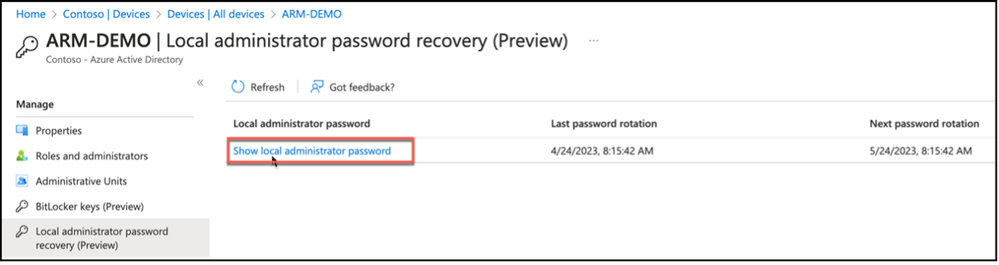
For Azure Active Directory, admin / operator can drill on the properties of the endpoint that its local administrator password is looked for; click on Local administrator password recovery link from the left hand side menu. This will bring information about the local administrator password such as when the last password rotation was and when the next password rotation will be, as well as an option to Show local administrator password.
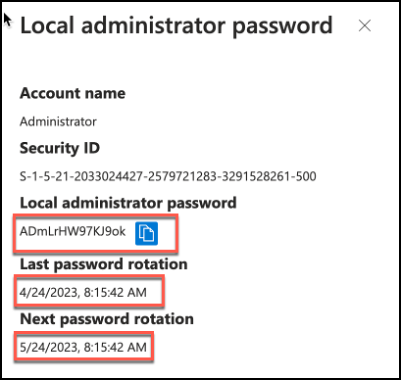
When clicked on Show local administrator password task, a window will pop-up from the right side of the screen and will Show details about the managed identity such as Account name, SID information, password rotation details as well as local admin password hidden in asterisk with a “Show” button.

Clicking on Show button will reveal the current local administrator password for the endpoint. Admin / Operator user can then use Copy button to copy the local administrator password to clipboard and use it to do the tasks that require administrator privileges.
Once the password is used to authentication to the target system, actions defined in post authentication actions policy setting will be executed after a time period defined in post authentication actions delay policy setting. These actions may include rotating password, logging off the managed identity or rebooting the device.
It is also possible to manually trigger local administrator password rotation. Task for Windows LAPS password rotation can be found in the actions menu item for the given endpoint.

Once clicked, admin / operator user will get a confirmation message stating that old password will no longer be applicable and a new password will be generated after rebooting the device.

It is also possible to access local administrator password via Microsoft Intune device properties. Let’s check how and confirm that password for local administrator has changed with rotate local admin password task.
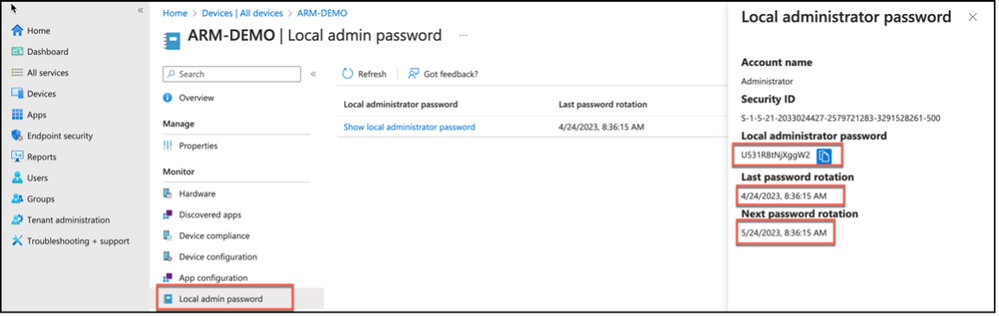
Device properties for a given device has an option for Local admin password. Which has the information about last rotation time for local administrator password, next rotation time for local administration password as well as Show local administrator password task just like the one in Azure Active Directory. Clicking on Show local administrator password task will reveal a similar pop-up from right hand side, that is usable to copy the existing local administrator password for the device.
Wrap Up:
Windows LAPS feature is released to Public Preview while this post is written. It has native support for cloud scenarios such as Hybrid Azure AD Joined devices and Azure AD Joined devices as well as interoperability with legacy LAPS solution. Customers may use Intune to create and deploy Windows LAPS policies and may utilize Azure AD or Microsoft Intune portals to view local administrator password for a given device. It is also possible to utilize Graph API to do certain tasks which can be a subject of another post.
